Multi tenant architecture is how most modern Software as a Service (SaaS) products scale: many customer accounts run on the same application, while each customer still feels like they have their own private system. Done well, it unlocks better margins, faster iteration, and a product that grows without you hiring a bigger team every quarter.
This guide shows you how to design a multi tenant architecture that is secure, upgradeable, and realistic for a small team.
Multi tenant architecture, explained in plain English
A tenant is a customer environment. Usually it maps to one company or one organization.
In a multitenant solution, multiple customers (tenants) use the same solution. Microsoft summarizes it plainly: "A multitenant solution is a solution used by multiple customers, or tenants" in its multitenant architecture overview.
This is closely tied to cloud computing itself. In NIST Special Publication 800-145, cloud "resource pooling" is defined as serving multiple consumers "using a multi-tenant model".
What multi tenant architecture is not:
-
Just "users and roles": Roles help with permissions, but multi-tenancy is about keeping one customer's data and experience separate from another customer's.
-
Only a database decision: Database isolation matters, but the harder problems are identity, routing, configuration, limits, and operations.
When multi tenant architecture is the right move (and when it is not)
Multi-tenancy works best when it supports your product strategy and your customer needs.
Choose it when:
-
You want repeatable revenue: Multi-tenant systems fit subscription products because you can onboard the next customer without cloning your entire stack.
-
Your customers are similar enough: If most workflows are shared, multi-tenancy keeps you sane.
-
You need centralized updates: One deploy upgrades everyone. That is a superpower when you are moving fast.
Avoid it (for now) when:
-
Each customer needs deep custom behavior: If every customer is a bespoke project, you are building an agency system, not SaaS.
-
You have strict isolation requirements early: Some regulated workloads are easier with single-tenant deployments.
-
You are still proving the product: An over-engineered tenant model can slow learning.
If you are in that last bucket, start with a simpler foundation and keep the upgrade path clear. A solid decision framework is covered in build vs buy for custom business software.
Silo vs pool vs bridge: pick your isolation model first
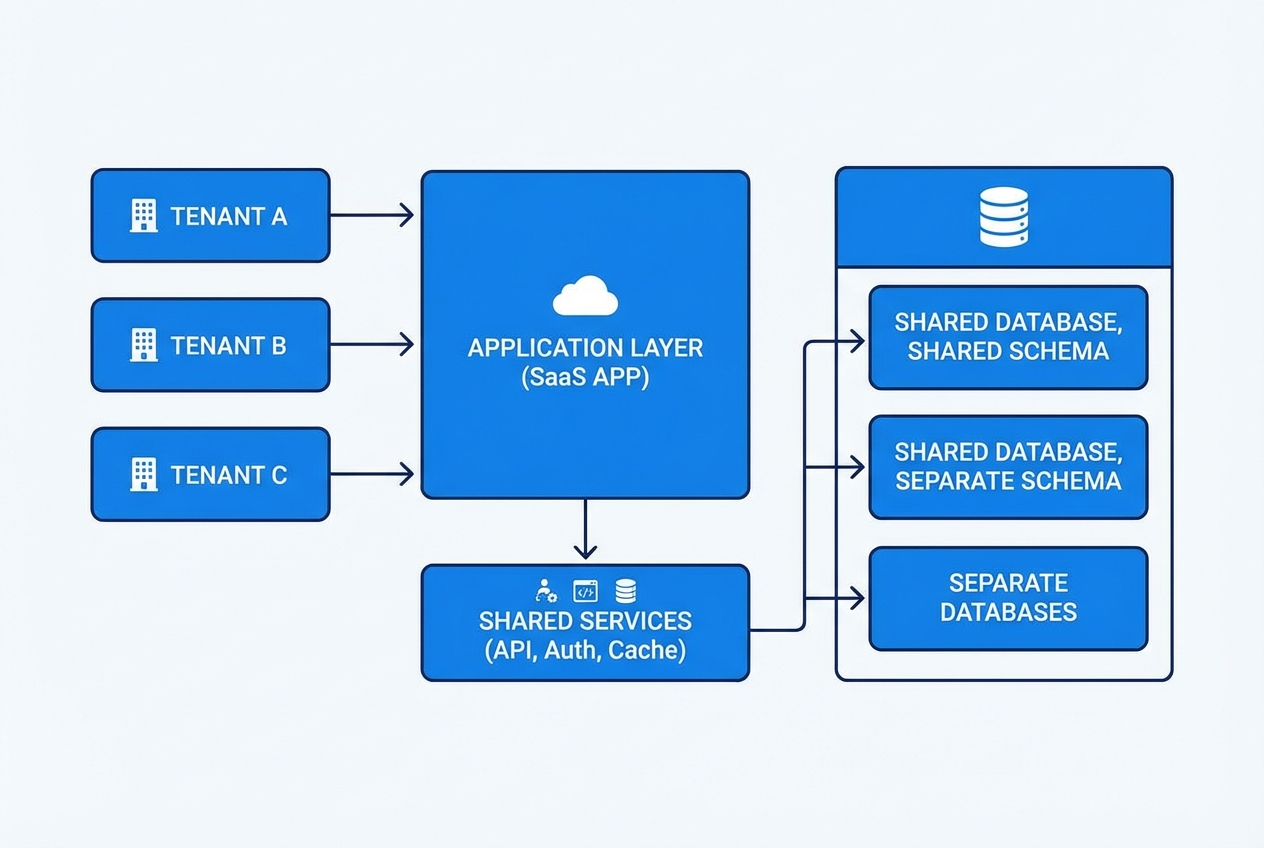
Multi-tenant architecture usually shares the app layer, then varies isolation at the data and infrastructure layers.
Your biggest early choice is how much infrastructure you share.
AWS groups SaaS tenancy patterns into three models: silo, pool, and bridge.
Here is what that means in practice:
| Model | What it means | Best for | Tradeoff |
|---|---|---|---|
| Pool | Tenants share most resources (app, compute, often database). | Early-stage SaaS, cost efficiency, fast iteration. | Harder to guarantee isolation, noisy-neighbor risk. |
| Silo | Tenants get dedicated resources (often dedicated database, sometimes dedicated stack). | Regulated workloads, high-value enterprise tenants. | Higher cost per tenant, more operational work. |
| Bridge | Hybrid. Some pooled, some siloed based on plan or risk. | Tiered offerings, gradual migration from pool to silo. | More complexity in routing and operations. |
A strong default for small teams is bridge. Start pooled. Silo the database or background jobs for premium tenants later.
How to design multi tenant architecture
This is the path that avoids rework. Each step builds a foundation you can keep.
1) Define what a "tenant" is in your product
Be explicit. A tenant is usually one company.
Decide these upfront:
-
Tenant identifier: A stable ID (for example,
tenant_id) used everywhere. -
Tenant boundary: What data belongs to a tenant, and what does not (for example, global templates or a public marketplace).
-
Tenant lifecycle: Create, suspend, delete, export.
Expected outcome: every request and every row of data has a clear tenant context.
2) Choose your identity approach (and attach tenant context to every request)
Identity is where tenant boundaries often break.
Common approaches:
-
Single sign-on (SSO): Let companies log in via a provider like Google Workspace or Microsoft Entra ID.
-
Email and password: Still fine, but you need consistent tenant assignment.
Make sure you can always answer: "Which tenant is this request for?"
Typical patterns:
-
Subdomain routing:
tenantA.yourapp.commaps to tenant A. -
Path routing:
yourapp.com/t/tenantA/.... -
Header-based routing (API): An
X-Tenant-Idheader, combined with server-side auth.
Expected outcome: you can derive tenant context without guessing.
3) Pick the data isolation pattern that matches your risk
This is the part most founders think about first, but it should come after tenant identity.
Here are the practical options:
| Data pattern | How it works | Why you would choose it | Where it bites you later |
|---|---|---|---|
| Shared database, shared schema | One database. Tables include a tenant_id column. | Cheapest, simplest to operate, great for MVP. | One bad query can leak data if you miss tenant filters. |
| Shared database, separate schema per tenant | One database, many schemas. | Better logical separation, easier per-tenant migrations in some stacks. | Schema sprawl, harder reporting across tenants. |
| Separate database per tenant | Each tenant has its own database. | Strong isolation, easier compliance stories. | Backups, migrations, and cost grow with tenant count. |
Expected outcome: a deliberate tradeoff between speed, safety, and ops cost.
4) Enforce tenant isolation in code, not in developer discipline
"Everyone remembers to add WHERE tenant_id = ..." is not a strategy.
Build guardrails:
-
Data access layer enforcement: Use an Object-Relational Mapping (ORM) pattern or query builder that requires tenant context.
-
Row-level security: If your database supports it, enforce tenant rules inside the database.
-
Tenant-aware caches: Cache keys must include tenant context.
Expected outcome: isolation becomes a system property.
5) Design configuration as a first-class system
Tenants often want differences:
-
Branding: Store logo, colors, and typography per tenant so customization stays clean.
-
Feature access by plan: Keep plan logic in one place so upgrades do not break permissions.
-
Custom workflows: Make workflow steps configurable so you do not fork code per customer.
Do not hardcode this in dozens of if statements.
Instead:
-
Tenant settings store: A
tenantstable and atenant_settingstable. -
Feature flags by plan: A simple plan-to-feature mapping that your app checks consistently.
-
Branding tokens: Colors, logo URL, and typography stored per tenant.
If you plan to offer reseller or white-label, this becomes critical. The patterns are laid out in white-label app builder guidance.
6) Implement Role-Based Access Control (RBAC) early
Role-Based Access Control (RBAC) defines what someone can do.
Minimum you need:
-
Role definitions: Admin, manager, member.
-
Permissions list: Actions like
invoice.read,invoice.write. -
Tenant-scoped assignments: Roles are tied to users inside a tenant.
Expected outcome: you can sell higher-tier plans safely because permissions are reliable.
7) Plan for limits: rate limiting, quotas, and noisy neighbors
Multi-tenant systems fail when one tenant consumes too much.
Build limits with intention:
-
Rate limiting: Protect APIs and logins from spikes.
-
Quotas: Storage limits, seat limits, usage-based metering.
-
Background job fairness: Separate queues or priority tiers.
Expected outcome: one tenant cannot degrade everyone else.
8) Make observability tenant-aware
Observability is your ability to understand what is happening in production.
You need tenant context on:
-
Logs: Add tenant identifiers to every log line so support can trace issues fast.
-
Metrics: Tag performance and usage metrics by tenant so you can spot noisy neighbors.
-
Traces: Include tenant context in distributed traces to see where latency appears per tenant.
-
Error reports: Attach tenant context to exceptions so you can reproduce problems in the right scope.
Expected outcome: when a customer says "it is slow," you can isolate the issue to their tenant and fix it fast.
Security: prevent "isolation escape" by design
Multi tenant architecture turns app bugs into business risk. A cross-tenant data leak can end trust overnight.
OWASP calls this out directly. Its Cloud Tenant Isolation project focuses on preventing "isolation escape" and cross-tenant vulnerabilities (OWASP Cloud Tenant Isolation).
Build security around these real failure modes:
-
Broken object-level authorization: A user can request another tenant's object by guessing an ID.
-
Missing tenant scoping in admin tools: Internal dashboards accidentally bypass tenant checks.
-
Shared secrets: One tenant's integration keys stored or logged in a way that exposes them.
Practical protections that pay off:
-
Tenant-scoped IDs: Use IDs that are checked against tenant context, not just "does this record exist".
-
Defense in depth: Enforce at API layer and database layer when possible.
-
Testing for cross-tenant access: Write automated tests that attempt forbidden access across tenants.
Operations that keep multi-tenancy from becoming a trap
A working tenant model shapes how you deploy, run migrations, and recover when something breaks.
Design these early:
-
Migrations: Decide how schema changes roll out. In pooled models, one migration affects everyone. In silo models, you need tooling to roll out per-tenant.
-
Backups and restores: You should be able to restore one tenant without restoring the world, even if the data is pooled.
-
Data export: Give tenants a clean way to leave. It reduces churn fear and helps enterprise sales.
-
Environment parity: Staging should mirror production tenancy patterns so you can catch isolation bugs before customers do.
Build a multi-tenant MVP fast without boxing yourself in
If you are trying to ship a SaaS offer quickly, ship a tenant model that can grow, then tighten the rare isolation edge cases once you have traction.
A practical approach for many founders:
-
Start pooled at the app layer: One codebase, one deployment pipeline.
-
Choose a data pattern with an upgrade path: Shared schema can work, as long as you enforce tenant scoping and keep a clean abstraction for the data layer.
-
Add bridge options later: Move premium tenants to dedicated databases or dedicated workers when they earn it.
If you want to prototype this in days, Quantum Byte's AI app builder can help you get the first version running from natural language, then refine it with real user feedback. When you hit the "this needs real engineering" moment, Quantum Byte's in-house development team can harden tenant isolation, migrations, and observability without restarting the build.
If you are ready to map your tenant model into a real product spec and start building, you can create a plug-and-play here, or explore enterprise solutions here.
For a clearer picture of how conversational building works before you commit, see how an AI app builder works.
Common multi-tenant mistakes
These are the ones that quietly kill momentum.
-
Tenant model timing: If you bolt on multi-tenancy after you have real customers, you will rewrite core assumptions. Define tenant identity and scoping from day one.
-
Shared database without guardrails: Shared schema is fine. Missing tenant enforcement is not. Put tenant checks in your data layer and tests.
-
Tenant vs user confusion: Tenants are customer organizations. Users live inside tenants. Keep the vocabulary strict so your code stays strict.
-
Missing tenant-aware observability: Without tenant context in logs and metrics, support becomes guesswork and churn increases.
-
No upgrade path: Even if you start pooled, design so you can move one tenant to a dedicated database or dedicated worker later.
If you are still deciding whether you should build this at all, or buy a tool, use this build vs no-code comparison to pressure-test the decision.
A clear next step
Multi tenant architecture is a growth lever when you design it deliberately. You learned how to:
-
Define tenants and tenant context: Lock down what a tenant is, how it is identified, and how every request stays scoped.
-
Choose a silo, pool, or bridge isolation strategy: Pick a sharing model that fits your current stage while keeping room for enterprise needs.
-
Pick data partitioning that matches your risk: Decide whether tenants share schemas or databases based on leak risk and operational load.
-
Enforce isolation with guardrails, not discipline: Make cross-tenant access hard to do by accident through code patterns, database controls, and tests.
-
Build tenant-aware security and operations: Plan migrations, backups, support workflows, and monitoring so you can scale safely.
If your goal is to productize your expertise into software, multi-tenancy is often the backbone that lets you serve more customers without taking on more chaos. Pair this with a product strategy like productizing consulting and you have a clear path to scalable revenue.
Frequently Asked Questions
What is the difference between multi-tenant and single-tenant architecture?
Single-tenant architecture gives each customer dedicated application resources (often a dedicated stack or database). Multi tenant architecture shares application resources across customers while still enforcing data and access isolation so tenants cannot see or affect each other.
Is multi-tenant architecture the same as a shared database?
No. A shared database is only one possible implementation. Multi-tenancy is an end-to-end design that includes identity, request routing, authorization, configuration, isolation, and operations. You can be multi-tenant with separate databases per tenant, too.
What is the safest database model for multi-tenancy?
Separate databases per tenant generally provide stronger isolation boundaries, but they increase operational work and cost. Many teams start with a shared database and shared schema, then move high-value tenants to dedicated databases in a bridge model.
How do you prevent cross-tenant data leaks?
Preventing leaks requires tenant context on every request, strong authorization checks, and guardrails in the data access layer so queries cannot forget tenant scoping. OWASP highlights this risk as "isolation escape" in its Cloud Tenant Isolation project.
When should you switch from pooled to siloed tenants?
Switch when a tenant's risk profile or value justifies dedicated resources. Common triggers include compliance needs, performance isolation requirements, large data volumes, or premium pricing tiers that can fund the extra infrastructure and operational overhead.
